ESET Bridge (ESET Proxy) Configuration
Installation on Windows (standalone installer)
Install ESET Bridge on a computer running a supported OS. |
1.Visit the ESET PROTECT download section to download a standalone ESET Bridge installer for Windows (ESETBridge_nt64.msi).
2.Run the ESETBridge_nt64.msi installer and click Next.
3.Click Privacy Policy to read the Privacy Policy. Read the End User License Agreement, select I accept the terms in the License Agreement and click Install.
4.Wait a few seconds until ESET Bridge is installed. When the installation is complete, click Finish.
In ESET PROTECT Web Console > Computers, there is an icon ![]() next to the name of the computer running ESET Bridge.
next to the name of the computer running ESET Bridge.
Note the hostname and IP address of the computer running ESET Bridge. After the installation, configure ESET Bridge for desired functionality.
If the installation is unsuccessful, see Troubleshooting.
ESET Bridge Policy (Assigned to ESET Proxy server)
You can configure ESET Bridge only remotely from ESET PROTECT On-Prem using an ESET Bridge Policy:
If there is an existing ESET Bridge Policy in place, you can: •Request the applied ESET Bridge configuration to see the current ESET Bridge configuration. •Edit the existing ESET Bridge Policy instead of creating a new one. |
1.Open the ESET PROTECT Web Console in your web browser and log in.
2.Click Policies > New Policy.
3.In Basic, type the Name. You can also type the Description and Select tags.
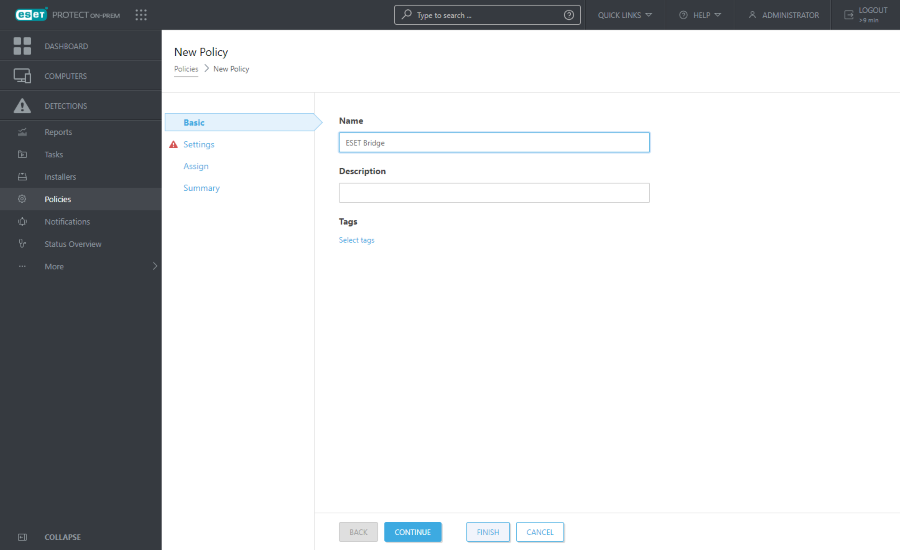
4.Click Settings and select ESET Bridge from the Select product drop-down menu.
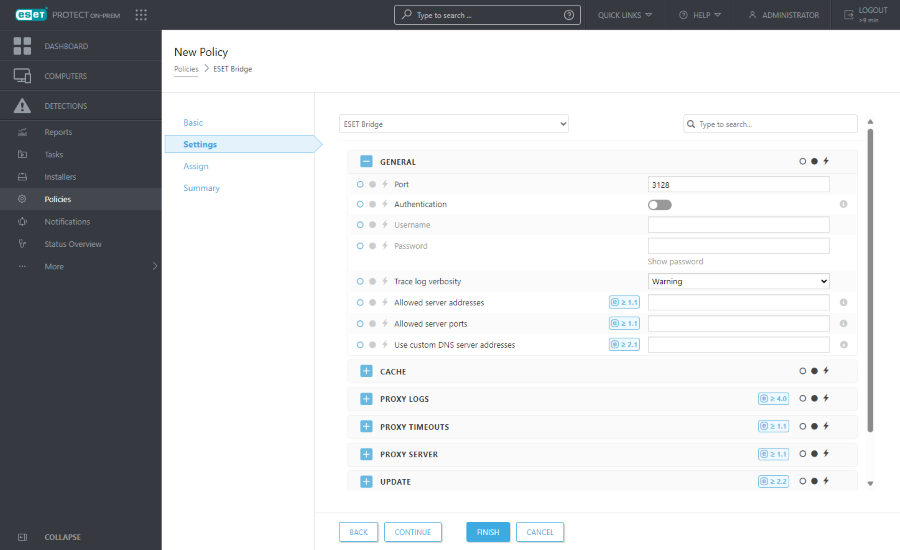
5.Configure ESET Bridge Policy settings:
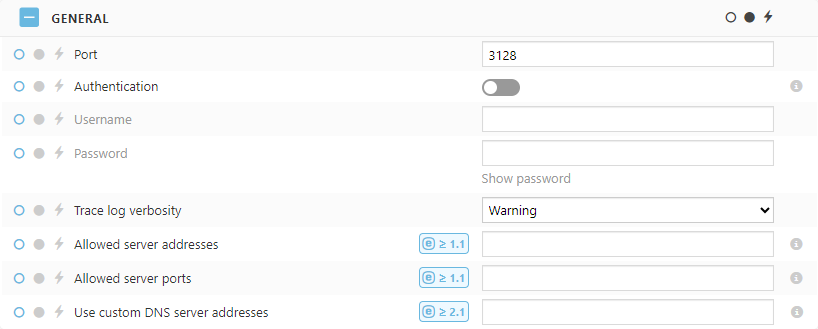
•Port—By default, ESET Bridge uses port 3128. You can set a custom port.
•Authentication—By default, there is no proxy server authentication. Enable the toggle and type the Username and Password to enable the authentication.
•Trace log verbosity—Select the trace log verbosity level from the drop-down menu: 0 (turn the logging off), Debug, Information (default), Warning, Error, Fatal. •Allowed server addresses—ESET Bridge has a default deny policy for the requests passing through, and only ESET hosts are allowed by default. To allow additional server addresses (hostnames), type domain names, fully qualified domain names, or IP addresses (separate addresses by a comma). •Allowed server ports—By default, ESET Bridge only allows ports used by the ESET servers. To allow additional ports (for example, a custom ESET PROTECT On-Prem port), type port numbers (separate ports by a comma).
•Use custom DNS server addresses—Use custom DNS servers instead of the default DNS servers found on the ESET Bridge computer. Type custom DNS server addresses as domain names or IP addresses separated by a comma. |
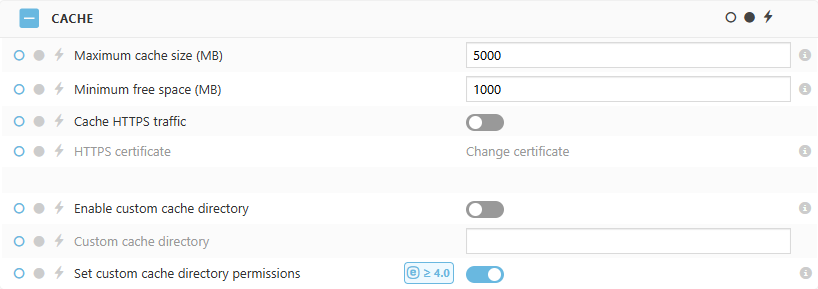
•Maximum cache size (MB)—The default and recommended value is 5000. If the cache size exceeds the set maximum cache size, the oldest cached data will be removed.
•Minimum free space (MB)—The default value is 1000. If the free space goes under the set minimum space, the least recently used cached data will be removed.
•Cache HTTPS traffic—Enable the toggle to enable HTTPS traffic caching.
•HTTPS Certificate—Add or change a peer certificate required for HTTPS traffic caching.
•Enable custom cache directory—Enable the toggle and type the Custom cache directory to store cache files in a custom directory. By default, ESET Bridge stores the cache files in the eset_cache directory: oWindows: C:\ProgramData\ESET\Bridge\Proxies\Nginx\data\eset_cache oLinux: /var/opt/eset/bridge/nginx/data/eset_cache
•Set custom cache directory permissions—Enable the toggle to set all the necessary permissions for the custom cache directory. If the directory does not exist, it will be created. This feature is available only on Windows.
|
•Custom proxy logs directory—Type a custom path for the Nginx proxy logs. By default, the proxy logs directories are: oWindows: C:\ProgramData\ESET\Bridge\Proxies\Nginx\logs oLinux: /var/opt/eset/bridge/nginx/logs
•Set proxy logs directory permissions—Enable the toggle to set all the necessary permissions for the custom logs directory. If the directory does not exist, it will be created. This feature is available only on Windows.
|
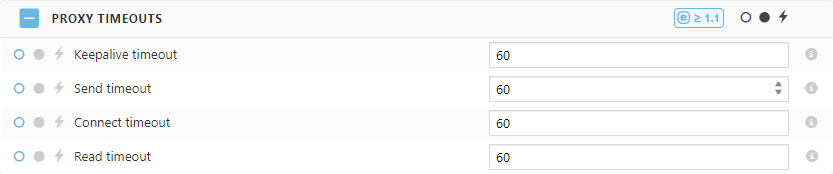
•Keepalive timeout—Set a timeout during which a keepalive client connection will stay open on the proxy side (in seconds; the default value is 60). The zero value disables keepalive client connections. •Send timeout—Set a timeout for transmitting a response to the client (in seconds; the default value is 60). The timeout is set only between two successive write operations, not for the transmission of the whole response. If the client does not receive anything within this time, the connection is closed. •Connect timeout—Set a timeout for establishing a connection with a proxied server (in seconds; the default value is 60). •Read timeout—Set a timeout for reading a response from the proxied server (in seconds; the default value is 60). The timeout is set only between two successive read operations, not for the transmission of the whole response. If the proxied server does not transmit anything within this time, the connection is closed. |
•Use proxy server—Enable the toggle to connect ESET Bridge via a proxy server (the proxy chaining feature). •Proxy server—Specify the remote proxy server hostname or IP address. •Port—Specify the remote proxy port.
|
•Auto-updates—Enable the toggle to enable ESET Bridge auto-updates. ESET Bridge (version 3 and later) supports auto-updates, which are enabled by default. When a more recent ESET Bridge version is available, ESET Bridge is automatically upgraded. |
6.Click Assign and assign the computer running ESET Bridge as the policy target.
7.Click Finish, or click Summary to see the policy overview and then click Finish.
Request the applied ESET Bridge configuration to see the current ESET Bridge configuration.
ESET Management Agent Policy
Follow the steps below to set up ESET Management Agent Policy to use ESET Bridge as a Proxy.
1.Open the ESET PROTECT Web Console in your web browser and log in.
ESET PROTECT All-in-one installer and Virtual Appliance (when ESET Bridge is enabled during the Virtual Appliance deployment) create default HTTP Proxy Usage policies for ESET Management Agent and ESET security products applied to the All Static Group. The policies automatically configure ESET Management Agents and ESET security products on managed computers to use ESET Bridge as a proxy server for caching update packages. The HTTPS traffic caching is enabled by default: •The ESET Bridge policy contains the HTTPS certificate, and the Cache HTTPS Traffic toggle is enabled. •The ESET Endpoint for Windows HTTP Proxy Usage policy contains the Certificate Authority for the HTTPS traffic caching. If you have existing policies that apply to all Agents and computers, edit your existing policies rather than create new ones. In Policies, click the ESET Management Agent HTTP Proxy Usage policy > select |
2.Click Policies > New Policy.

3.In Basic, type the Name. You can also type the Description and Select tags.

4.Click Settings and select ESET Management Agent from the Select product drop-down menu.
5.Expand Advanced Settings. Select an option from the Proxy Configuration Type drop-down menu under HTTP Proxy:
•Global Proxy—Use a single ESET Bridge as a proxy solution for caching downloads and forwarding Agent communication.
•Different Proxy Per Service—Use a separate ESET Bridge as a proxy for Agent replication (forwarding communication) and another ESET Bridge for caching of ESET services (for example, updates).
ESET PROTECT On-Prem Online Help contains a detailed description of all ESET Management Agent Policy settings. |
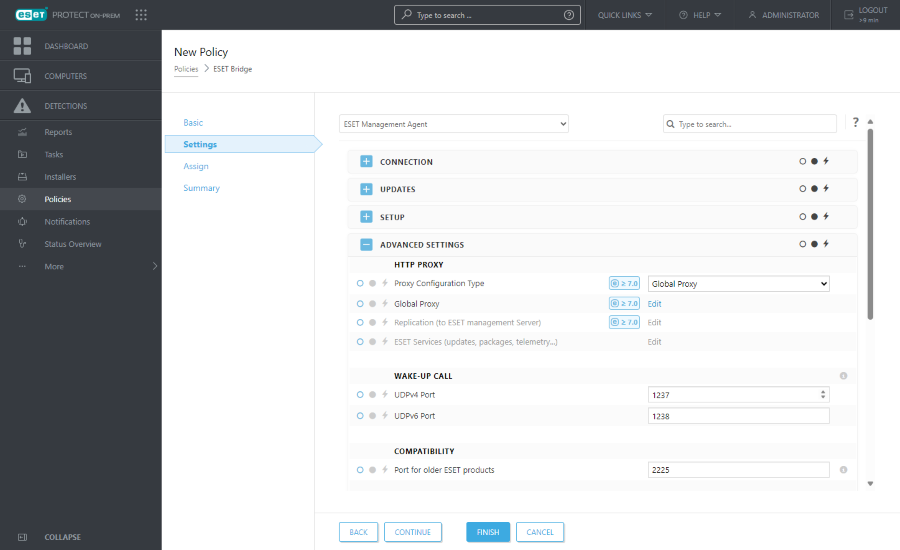
6.Follow the steps based on your previous selection:
7.Click Assign and assign the computers or groups as the policy targets. ESET Management Agents on the assigned computers will use ESET Bridge as a proxy (as configured in this policy).
8.Click Finish, or click Summary to see the policy overview and then click Finish.
When ESET Management Agents on managed computers receive the policy, they will connect to ESET Bridge.
ESET security product policy
Follow the steps below to set up ESET security product policy to use ESET Bridge as a global proxy for network traffic forwarding and caching ESET security product updates.
1.Open the ESET PROTECT Web Console in your web browser and log in.
ESET PROTECT All-in-one installer and Virtual Appliance (when ESET Bridge is enabled during the Virtual Appliance deployment) create default HTTP Proxy Usage policies for ESET Management Agent and ESET security products applied to the All Static Group. The policies automatically configure ESET Management Agents and ESET security products on managed computers to use ESET Bridge as a proxy server for caching update packages. The HTTPS traffic caching is enabled by default: •The ESET Bridge policy contains the HTTPS certificate, and the Cache HTTPS Traffic toggle is enabled. •The ESET Endpoint for Windows HTTP Proxy Usage policy contains the Certificate Authority for the HTTPS traffic caching. If you have existing policies that apply to all Agents and computers, edit your existing policies rather than create new ones. In Policies, click the ESET security product (for example, ESET Endpoint for Windows) HTTP Proxy Usage policy > select |
2.Click Policies > New Policy.

3.In Basic, type the Name. You can also type the Description and Select tags.

4.Click Settings and select ESET Endpoint for Windows from the Select product drop-down menu.
The steps below show the ESET Endpoint Antivirus/Security for Windows policy configuration. You can similarly configure a policy for another ESET security product. |
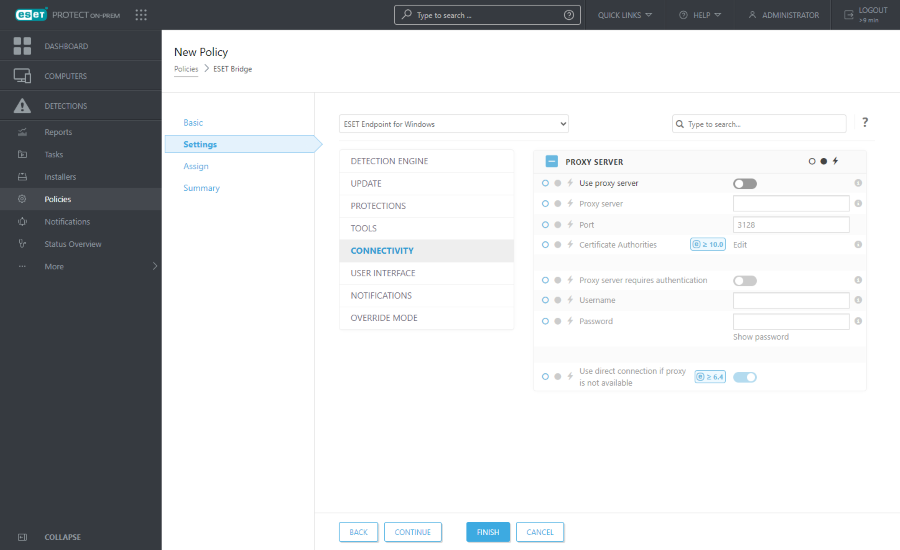
5.Click Connectivity > Proxy Server to define global proxy server settings for all ESET security product modules that require an internet connection:
a.Enable the toggle next to Use proxy server.
b.Type the IP address or fully qualified domain name (FQDN) of the server where ESET Bridge is installed in the Proxy server field.
c.Ensure the port number matches the Port defined in the ESET Bridge Policy (default: 3128).
d.Click Edit next to Certificate Authorities and add the ESET PROTECT Certification Authority to enable HTTPS traffic caching. ESET security products use the Certification Authority to validate the peer certificate from the ESET Bridge Policy.
e.If you created a Username and Password in the ESET Bridge Policy, type them in the appropriate fields. (Enable the toggle next to Proxy server requires authentication).
f.Keep the toggle next to Use direct connection if proxy is not available enabled to allow this fallback option (recommended). If you have configured the ESET security product to connect via proxy (ESET Bridge) and the proxy is unreachable, the ESET security product will bypass the proxy and communicate directly with ESET servers.
You can also set up proxy server settings under Update > Profiles > Updates > Connection options by selecting Connection through a proxy server from the Proxy mode drop-down menu. This setting applies to the given update profile, and we recommend it for laptops that often receive detection engine updates from remote locations. |
6.Click Assign and assign the computers or groups as the policy targets. ESET security products on the assigned computers will use ESET Bridge as a proxy (as configured in this policy).
7.Click Finish, or click Summary to see the policy overview and then click Finish.
When managed computers with ESET security products receive the policy, they will connect to ESET Bridge.
Jerome Antiado
ESET Technical Engineer
Related Articles
Download, install and activate ESET Cyber Security
Issues Install ESET Cyber Security version 7 Solution Install ESET Cyber Security version 7 Uninstall any previously installed antivirus software on your system. Download version 7 of ESET Cyber Security and double-click the appropriate installer ...Activate ESET home and small office products for Windows using the Activation key
If you skipped activation during the installation, follow the steps below: Open the main program window of your ESET Windows product. When the product activation screen appears, click Use a purchased activation key. Figure 1-1 Type or copy/paste your ...Enable ESET LiveGuard Advanced for ESET Mail Security
Enable and Configure ESET LiveGuard Advanced for ESET Mail Security - Log in to your ESET Protect Web Console. - Click Configuration/Policies → New policy. - Type a name for your policy. The Description field is optional. - Select the Product: In the ...Reset the ESET Protect On-Prem Password
Click Start → Windows System → Control Panel. Figure 2-1 Click Programs and Features. Figure 2-2 Right-click ESET PROTECT Server and select Change from the context menu. Figure 2-3 Click Next. Figure 2-4 Click Repair. Figure 2-5 Complete all required ...Reset a user Key-File password in ESET Endpoint Encryption
Issue You lost or forgot the key-file password to log in to a managed ESET Endpoint Encryption (EEE) instance (i.e. your EEE software was installed by a member of your IT department) Solution ESET Endpoint Encryption Server administrators: Log in to ...